SaaS Security
- Category - Uncategorized

SaaS Security
Security for SaaS customers is a high priority and is
treated as such. In this article we will
review the many aspects of security standards that are involved when a customer
opts to use ARMS from our Cloud/SaaS environment.
Microsoft Azure Government Cloud
Azure Government is a cloud infrastructure isolated from the
commercially available Azure global cloud infrastructure. Because Azure
Government is reserved for use only by US government entities, It operates from
datacenters that are both physically and logically isolated from the
commercially available Azure cloud datacenters.
Microsoft Azure Government compliance includes:
· CJIS
· CNSSI (sets national cybersecurity policy for US
gov entities)
· DoD L 2,4,5
· FedRAMP
· FIPS 140-2
Because it was one of the first CJIS certified cloud
environments, we have chosen MS Azure Government to host our customers and
provide the security that they need.
Data Protection
ARMS SaaS is designed to isolate all the data and servers
provisioned to a specific agency in a separate virtual environment. For each
agency, we use separate Resource Groups that include separate virtual machines,
separate virtual network, and separate storage for each agency; Tenants are
completely isolated.
The Azure platform in general uses a virtualized
environment, whereby workloads from different tenants run in isolation on
shared physical servers, to keep customers’ data secure in the environment.
Customer instances operate as standalone virtual machines that do not have access
to a physical host server, and this isolation is enforced by using physical
processor privilege levels.
Tenant Isolation
Within Azure, each ARMS SaaS customer is the single-tenant
of a Resource Group (RG), the collection of virtual infrastructure resources
which contribute to the overall functionality of the SaaS environment.

Includes the following basic Resources:
· Virtual Network
· Virtual Network Interface (NIC)
· Virtual Server
· Microsoft SQL Server Database
Resources in a Resource Group are isolated from interacting
with Resources located within another Resource Group; Resources in a Resource
Group only interact with Resources located within its same Resource Group.
Data Location
The ARMS SaaS implementation provides the agency with a
Primary Region and a Secondary Region. A region is a collection of physically
separated datacenters within certain proximity of one another. For example,
Microsoft Azure Government has 3 datacenters in Texas which, together, make up
what is referred to as the AzureGovTX Region. Within a region, the tenant of a
Resource Group has at least one other datacenter to which the tenant’s data and
applications are consistently replicated for increased uptime.
The ARMS team, as part of ARMS SaaS licensing, provides the
agency with two regions of systems: a primary (production, with replication
within) and a secondary (failover, with replication within). This
implementation provides the agency with a minimum of 4 physically separated
datacenters that are continuously replicated with the agency’s data and
applications for increased uptime. Within each datacenter, there are at least 3
physical host servers available for running the tenant’s data and applications.
So that gives us 3 hosts in a single datacenter, at least 2 datacenters in a
region, and 2 regions made a part of the ARMS SaaS environment for the
customer.
Doing the math: ARMS
SaaS = 4 datacenters / 12 physical host servers of the virtual environment
The secondary region is for business continuity and disaster
recovery planning and is initialized in the event of a severe outage of all the
datacenters and hosts in a primary region. This gives the tenant the fastest
route to being online again after a significant datacenter outage.
Data Protection
ARMS SaaS implements encryption of data-in-transit using FBI
CJIS Security Policy compliant and FIPS 140-2 compliant AES 256-bit encryption.
ARMS SaaS implements encryption of data-at-rest using FBI
CJIS Security Policy compliant and FIPS 140-2 compliant AES 256-bit encryption
as well. The data persisted to storage in Azure Government is encrypted using
Microsoft-managed keys (managed by the Azure Gov platform), meaning no vendor
personnel manages the encryption keys (i.e., the encryption keys are private).
Business Continuity and Disaster Recovery
ARMS SaaS has a documented Disaster Recovery Plan in place,
which includes
· Disaster classification
· Plan of remedial actions
· Procedures for periodic testing, review, and
revisions
· Procedures of emergency communication, incident
tracking, and post-mortems
The DR plan is based on Potential Disaster, Probability, and
Impact
· Ex: Region-wide service disruption –
Probability: 4 (Low), Impact: 3 (Medium)
Data Replication across Azure Government regions
To protect from potential Azure Region failure, ARMS SaaS
implements Disaster Recovery as failover to a secondary region – known as Azure
Site Recovery – where the agency’s primary region virtual environment is
continuously replicated to the secondary region
· Primary Region: located in one part of the
country (ex: Texas)
· Secondary Region: located in another part of the
country (ex: Virginia)
Azure Site Recovery depicted by the diagram below:
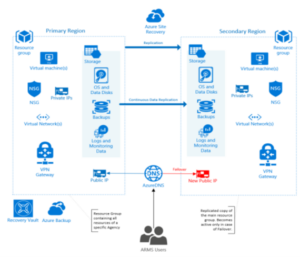
Using Azure Site Recovery service allows us to:
· Continuously replicate the entire infrastructure
to the secondary region
· Control when we want to fail-over to the
secondary region
· Control snapshot frequency and recovery point
retention period
o
point-in-time snapshot every 2 hours
o
maintain recovery points for 24 hours
· Perform periodic Disaster Recovery drills not
affecting live clients
· The process of fail-over and system health check
takes no more than 1 hour, which satisfies our RPO/RTO requirements (Recovery
Point Objective, Recovery Time Objective)
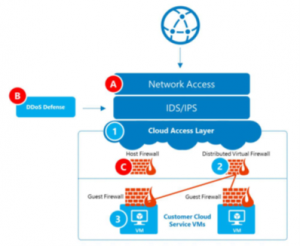
Intrusion Protection and Prevention
Microsoft Azure Government shares responsibility with the
ARMS team to provide layers of protection to the agency’s virtual environment
Microsoft provides physical and logical security of the
datacenter and host equipment
· Network Access Layer isolates Azure private
network from the internet
· Azure DDoS/DOS/IDS Layer provides prevention of
denial of service and intrusion detection
· Azure provides host firewalls and VLANs
· Azure enforces Multi-Factor Authentication among
its operators at the datacenter
Layers of Protection
Microsoft Azure Government shares responsibility with the
ARMS team to provide layers of protection to the agency’s virtual environment
· The Microsoft team provides physical datacenter protection
and Azure platform protection
· The ARMS team provides protection of the
agency’s virtual infrastructure
o Cloud Access Layer acts as the gateway from the
internet into the isolated private network, load balancing, firewall, and NAT
functionalities. ARMS SaaS uses Azure Application Gateway, Azure Web
Application Firewall, and Azure Security Center on the Cloud Access Layer.
o Virtual Network Layer is managed similar to an
on-premises private network.
§ There is the VM and its accompanied firewall,
IDS, and DoS solutions. Our team utilizes Azure Security Center to protect VMs.
§ Network Security Groups are used to filter
traffic based on separate NICs and/or VPN Gateway
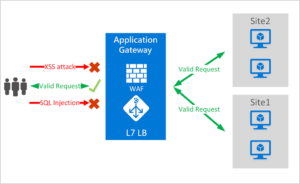
Azure Application Gateway and Web Application Firewall
Web Application Firewall (WAF) is a feature of Application
Gateway that provides centralized protection of the ARMS SaaS instance from
common exploits and vulnerabilities. WAF is based on rules from the OWASP (Open
Web Application Security Project) core rule sets 3.0 or 2.2.9
Although there is ARMS-application implemented protection
from common attack-types (like SQL Injection) at the application level (i.e.,
built into ARMS), WAF provides an additional layer of protection. WAF protects
against:
· SQL Injection
· Cross-Site Scripting
· HTTP request smuggling, response splitting, remote
file intrusion, protocol violations, anomalies, bots, crawlers, scanners, and
common app misconfigurations
Azure Security Center
Security Center provides a central view of the security
state of all Azure resources.
Breakthroughs in ‘Big Data’ and ‘Machine Learning’
technologies are leveraged to evaluate events across the entire cloud fabric –
detecting threats that would be impossible to identify using manual approaches
and predicting the evolution of attacks. These security analytics include:
· Integrated threat intelligence: looking for
known-bad actors by leveraging global intel
· Behavioral analytics: applies known patters to
discover malicious behavior
· Anomaly detection: uses statistical profiling to
build a historical baseline, alert on deviations from established baseline
Conclusion
As depicted in the breakdown of the many different levels of
security we offer our SaaS customers through ARMS and MS Azure, we take
security very seriously. If you have any
further questions or concerns, please do not hesitate to reach out to the ARMS
support team.

